How to Set Up SSO LDAP for Node-RED
Step-by-step guide on setting up SSO LDAP for your self-hosted FlowFuse platform

A few days ago, we published a blog explaining SSO and how to set up SAML for your self-hosted FlowFuse. Now, in this guide, we will walk you through the process of setting up SSO with LDAP for your self-hosted FlowFuse. We will use OpenLDAP as the provider and cover everything from introducing LDAP, how it works, installing and configuring OpenLDAP, managing users (create, delete, update), and finally setting up FlowFuse for SSO with LDAP.
Understanding LDAP SSO?
What is LDAP
LDAP (Lightweight Directory Access Protocol) is a protocol used to access and manage directory information. In the context of network administration, a directory service acts as a specialized database that stores and organizes information about users, devices, and other resources. Think of it as a digital phonebook for your network, allowing centralized management and efficient access to information.
LDAP enables applications and services to query, add, update, and delete directory entries stored on LDAP servers. It simplifies identity management by enabling easy authentication, authorization, and quick access to information across distributed systems.
How LDAP SSO works
-
User Authentication Request: A user attempts to access a service or application that requires authentication.
-
SSO Initiation: The application forwards the authentication request to the Identity Provider (IdP) configured with LDAP, such as OpenLDAP.
-
LDAP Authentication: The IdP (LDAP server) verifies the user's credentials against its directory.
-
Authentication Response: If the credentials are valid, the LDAP server sends an authentication response (usually a token or assertion) back to the application.
-
Access Granted: The application grants access to the user based on the authentication response received from the LDAP server.
Setting up SSO LDAP for FlowFuse
Before we proceed, ensure that FlowFuse is deployed on your server with an Enterprise license and you have ssh connection with it so that you can run commands on the server. If you haven't installed it yet, please check out our documentation on installing FlowFuse or our blog on deploying FlowFuse on Ubuntu with Docker.
Installing and Configuring OpenLDAP
Throughout this section, we will install and configure OpenLDAP on your Ubuntu server. Make sure to replace the commands and configs with your details. If you are using a different distribution, you can follow other resources available on the internet for installation and configuration, as well as managing of users.
-
Set the hostname for your LDAP server:
hostnamectl set-hostname ldap.<your-domain>.com -
Add the server IP to
/etc/hosts:echo '<your_server_ip> ldap.<your-domain>.com' >> /etc/hosts -
Install OpenLDAP and related utilities:
apt install slapd ldap-utils -
Set an administrator password for LDAP during installation and confirm it in the next prompt.
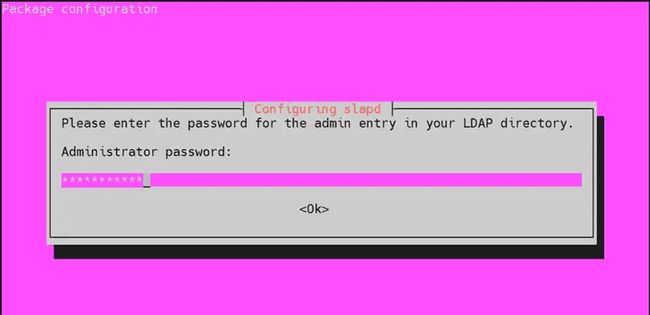
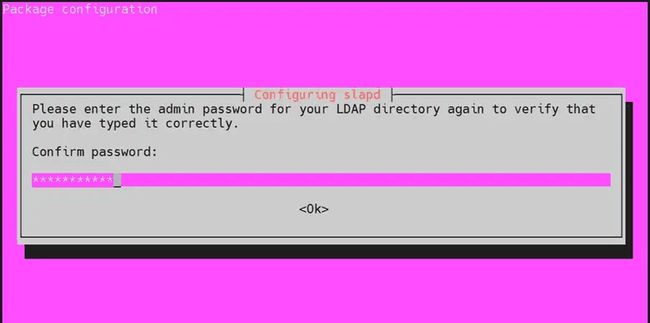
-
Reconfigure the slapd package:
dpkg-reconfigure slapd -
When asked to omit server configuration, select ‘NO’
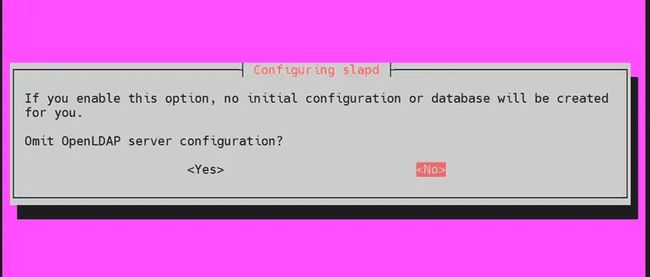
-
Configure the base DN (Distinguished Name) for your LDAP directory:
- Use your domain name to construct the base DN. For example, if your domain is
my-flows.site, the base DN would bedc=my-flows,dc=siteand press 'ENTER' to confirm.
- Use your domain name to construct the base DN. For example, if your domain is
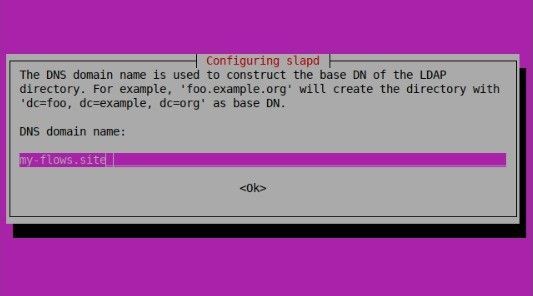
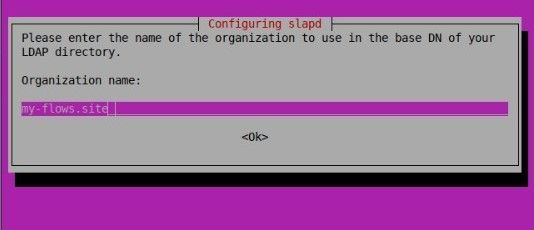
- Provide a name for your organization, which will also be part of the base DN and press 'Enter.'
- Enter the Administrator password for your LDAP directory.

- Confirm the password.

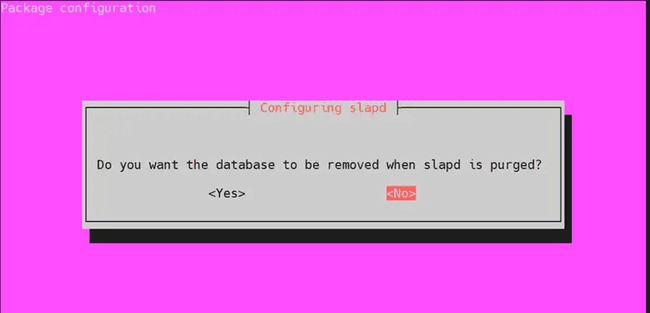
- When asked to remove the database when slapd is purged, select ‘NO’.
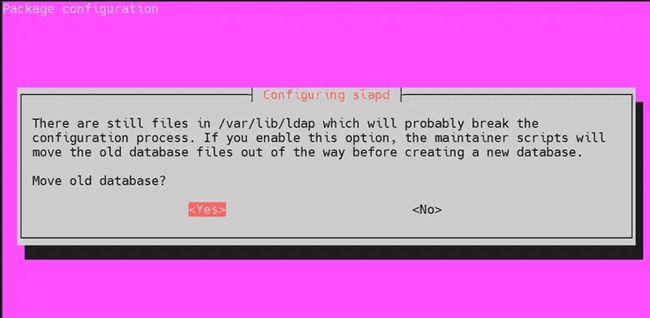
- Select ‘Yes’ to remove the old database to create room for a new database.
- Edit the main OpenLDAP configuration file:
sudo nano /etc/ldap/ldap.conf- Uncomment the lines beginning with “BASE” and “URI”, for example, my domain is
my-flows.site, we have updated the file as below, but you have to update it according to your domain:
BASE `dc=my-flows,dc=site.`
URI `ldap://ldap.my-flows.site.`
Adding, Updating, and Deleting Groups and Users
Adding Groups and Users
-
Create a file for the base groups and open the editor:
nano groups.ldif -
Add the following content to
groups.ldif, which will create theusersgroup, make sure when you create a new group the gidNumber and ou is unique:dn: ou=users,dc=my-flows,dc=site objectClass: organizationalUnit ou: users gidNumber: 7000 -
Add the groups to the LDAP directory:
ldapadd -x -D cn=admin,dc=my-flows,dc=site -W -f groups.ldif -
Create a password for the user and store the encrypted password:
Slappasswd -g-
Create a file for the user:
nano user.ldif -
Add the following content to user.ldif. Replace the placeholders with actual values for
uid,sn,givenName,displayName,cn,gecos,homeDirectory, and set userPassword to the password generated earlier. Ensure each user has a uniqueuidNumber, and you can keep the gidNumber the same if users belong to the same primary groupdn: uid=sumit,ou=users,dc=my-flows,dc=site objectClass: inetOrgPerson objectClass: posixAccount objectClass: shadowAccount uid: sumit sn: shinde givenName: sumit cn: sumit shinde displayName: sumit shinde uidNumber: 1000 gidNumber: 7000 userPassword: {SSHA}uQVjd8MLaJ7AXEd/grqViuKnk9tNojdy gecos: sumit shinde loginShell: /bin/bash homeDirectory: /home/sumit -
Save and exit the configuration file.
-
Add the user to the LDAP directory:
ldapadd -x -D cn=admin,dc=my-flows,dc=site -W -f user.ldif
Updating Groups and Users
-
Create a file for the user update:
nano user_update.ldif -
Add the following content to
user_update.ldifto update the user's details (e.g., changing the display name):dn: uid=sumit,ou=users,dc=my-flows,dc=site changetype: modify replace: displayName displayName: Sumit Rupesh Shinde -
Save and exit the configuration file.
-
Apply the update to the LDAP directory:
ldapmodify -x -D cn=admin,dc=my-flows,dc=site -W -f user_update.ldif -
Create a file for the group update:
nano group_update.ldif -
Add the following content to
group_update.ldifto update the group's details (e.g., changing the organizational unit name):dn: ou=users,dc=my-flows,dc=site changetype: modify replace: ou ou: staff -
Save and exit the configuration file.
-
Apply the update to the LDAP directory:
ldapmodify -x -D cn=admin,dc=my-flows,dc=site -W -f group_update.ldif
Deleting Groups and Users
-
Delete a user from the LDAP directory:
ldapdelete -x -D cn=admin,dc=my-flows,dc=site -W "uid=sumit,ou=users,dc=my-flows,dc=site" -
Delete a group from the LDAP directory:
ldapdelete -x -D cn=admin,dc=my-flows,dc=site -W "ou=users,dc=my-flows,dc=site"
Configuring and Enabling SSO in FlowFuse
- To configure FlowFuse with SSO, make sure you are logged in as an administrator.
- Go to Admin settings by clicking on the profile icon in the top-right corner and then selecting "Admin settings".
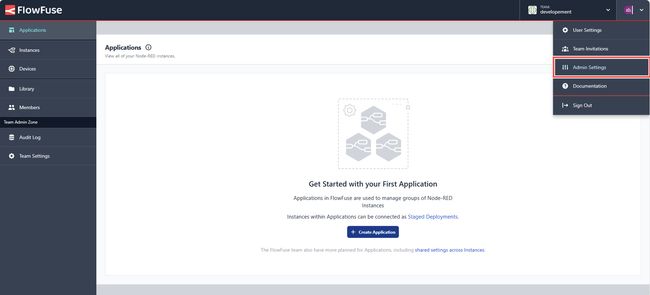
- Click on "Settings" from the left sidebar and switch to the SSO section.
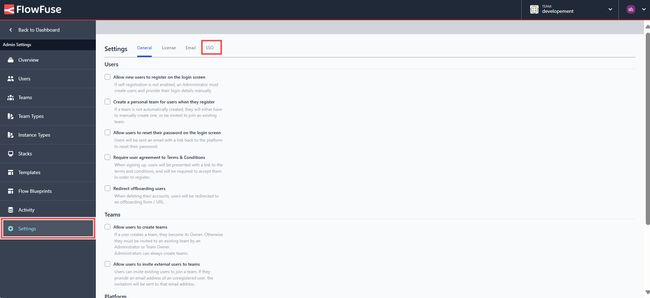
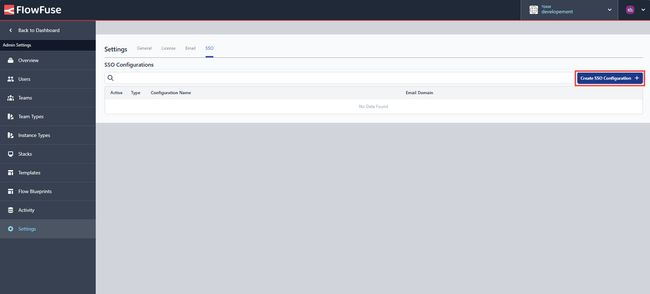
- Click on the top-right "Create SSO configuration".
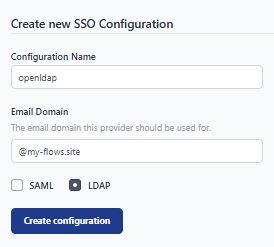
- Enter the name for your configuration, then enter the domain with
@prefix and select the "LDAP" option. Click on the "Create configuration" button.
- In the next form, in the server field enter
your-server-ip:389. 389 is the default port for LDAP but make sure to check it. If you are going to enable TLS, replace the port with 636.
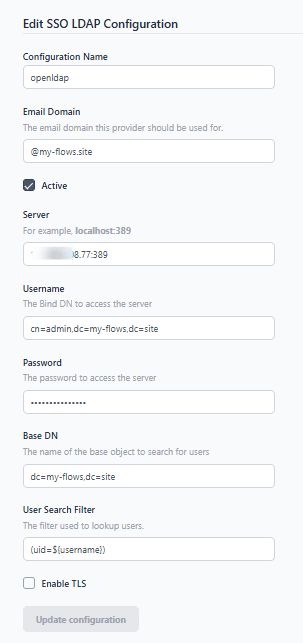
- Enter the the bind DN into the username field.
- Enter the password for the LDAP administrator in the password field.
- Enter the Base DN. For example, if your domain is
my-flows.site, the Base DN will bedc=my-flows,dc=site. - Click on the "Update configuration" button.
Signing in Using SSO
To sign in using SSO, users of your self-hosted FlowFuse must have a FlowFuse account created with an email ID associated with the domain configured with SSO. For more information, refer to creating users in FlowFuse.
- Open your platform in the browser. Enter the username in the username/email field.
- Click on "Login".
- Then enter the password set in the LDAP directory for that user.
Note: Admin users will still be able to log in with their original FlowFuse username/password - this ensures they don't get locked out of the platform if there is a problem with the SSO configuration
Conclusion
In this guide, we covered how to set up SSO with LDAP for your self-hosted FlowFuse platform using OpenLDAP. We installed and configured OpenLDAP, learned to managed groups and users, and configured SSO within FlowFuse. This setup enhances security by centralizing user authentication and simplifies access across applications, ensuring efficient user management in your FlowFuse deployment.
Got questions or need help setting up SSO LDAP for FlowFuse (Node-RED)? with us!
Talk to Us NowAbout the Author
Sumit Shinde
Technical Writer
Sumit is a Technical Writer at FlowFuse who helps engineers adopt Node-RED for industrial automation projects. He has authored over 100 articles covering industrial protocols (OPC UA, MQTT, Modbus), Unified Namespace architectures, and practical manufacturing solutions. Through his writing, he makes complex industrial concepts accessible, helping teams connect legacy equipment, build real-time dashboards, and implement Industry 4.0 strategies.